Background
This is more than just a malware analysis blog post. Morelike a threat report or updates of a cyber crime group activity that continuing their malicious operation and distribution method, that we think people who use internet must aware about.
The spam driven credentials/PWS stealer group we track, that is known for infecting trojan to steal credential via Blackhole Exploit Exploit Kit, that is responsible to the infection of recent fake FedEx, fake Amazon ticket, fake BBB, fake American Express spams and so on, is recently making a brand new new campaign through the below "real" malware infector domains:
fuigadosi.ru (NEW)Currently (see the NEW tagged domains) are active for infecting:
faneroomk.ru (NEW)
fzukungda.ru (NEW)
famagatra.ru (NEW)
fulinaohps.ru (NEW)
finalions.ru (NEW)
emmmhhh.ru (NEW)
errriiiijjjj.ru (NEW)
ejjiipprr.ru (NEW)
eiiiioovvv.ru (NEW)
"previous infector used historically:"
emaianem.ru
enakinukia.ru
exibonapa.ru
esigbsoahd.ru
egihurinak.ru
exiansik.ru
emaianem.ru
estipaindo.ru
epilarikko.ru
eminakotpr.ru
ewinhdutik.ru
efjjdopkam.ru
eipuonam.ru
epionkalom.ru
ejiposhhgio.ru
emalenoko.ru
eminakotpr.ru
:
Tracing to fzukungda.ru[a] via a.root-servers.net., maximum of 1 retries
a.root-servers.net. (198.41.0.4)
|\___ e.dns.ripn.net [ru] (2001:0678:0015:0000:0193:0232:0142:0017) Not queried
|\___ e.dns.ripn.net [ru] (193.232.142.17)
| |\___ ns2.fzukungda.ru [fzukungda.ru] (110.164.58.250) Got authoritative answer
| |\___ ns4.fzukungda.ru [fzukungda.ru] (203.171.234.53) Got authoritative answer
| |\___ ns3.fzukungda.ru [fzukungda.ru] (210.71.250.131) Got authoritative answer
| |\___ ns5.fzukungda.ru [fzukungda.ru] (184.106.195.200) *
| \___ ns1.fzukungda.ru [fzukungda.ru] (41.168.5.140) Got authoritative answer
|\___ a.dns.ripn.net [ru] (2001:0678:0017:0000:0193:0232:0128:0006) Not queried
|\___ a.dns.ripn.net [ru] (193.232.128.6)
| |\___ ns1.fzukungda.ru [fzukungda.ru] (41.168.5.140) (cached)
| |\___ ns3.fzukungda.ru [fzukungda.ru] (210.71.250.131) (cached)
| |\___ ns4.fzukungda.ru [fzukungda.ru] (203.171.234.53) (cached)
| |\___ ns2.fzukungda.ru [fzukungda.ru] (110.164.58.250) (cached)
| \___ ns5.fzukungda.ru [fzukungda.ru] (184.106.195.200) *
: :
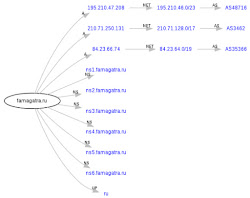
Tracing to famagatra.ru[a] via a.root-servers.net., maximum of 1 retries
a.root-servers.net. (198.41.0.4)
|\___ b.dns.ripn.net [ru] (2001:0678:0016:0000:0194:0085:0252:0062) Not queried
|\___ b.dns.ripn.net [ru] (194.85.252.62)
| |\___ ns4.famagatra.ru [famagatra.ru] (203.171.234.53) Got authoritative answer
| |\___ ns1.famagatra.ru [famagatra.ru] (41.168.5.140) Got authoritative answer
| |\___ ns5.famagatra.ru [famagatra.ru] (184.106.195.200) *
| |\___ ns2.famagatra.ru [famagatra.ru] (110.164.58.250) Got authoritative answer
| \___ ns3.famagatra.ru [famagatra.ru] (210.71.250.131) Got authoritative answer
|\___ f.dns.ripn.net [ru] (2001:0678:0014:0000:0193:0232:0156:0017) Not queried
|\___ f.dns.ripn.net [ru] (193.232.156.17)
| |\___ ns2.famagatra.ru [famagatra.ru] (110.164.58.250) (cached)
| |\___ ns5.famagatra.ru [famagatra.ru] (184.106.195.200) *
| |\___ ns1.famagatra.ru [famagatra.ru] (41.168.5.140) (cached)
| |\___ ns4.famagatra.ru [famagatra.ru] (203.171.234.53) (cached)
| \___ ns3.famagatra.ru [famagatra.ru] (210.71.250.131) (cached)
: :
Tracing to fulinaohps.ru[a] via a.root-servers.net., maximum of 1 retries
a.root-servers.net. (198.41.0.4)
|\___ f.dns.ripn.net [ru] (2001:0678:0014:0000:0193:0232:0156:0017) Not queried
|\___ f.dns.ripn.net [ru] (193.232.156.17)
| |\___ ns3.fulinaohps.ru [fulinaohps.ru] (210.71.250.131) Got authoritative answer
| |\___ ns5.fulinaohps.ru [fulinaohps.ru] (184.106.195.200) *
| |\___ ns2.fulinaohps.ru [fulinaohps.ru] (110.164.58.250) Got authoritative answer
| |\___ ns1.fulinaohps.ru [fulinaohps.ru] (41.168.5.140) Got authoritative answer
| \___ ns4.fulinaohps.ru [fulinaohps.ru] (203.171.234.53) Got authoritative answer
|\___ b.dns.ripn.net [ru] (2001:0678:0016:0000:0194:0085:0252:0062) Not queried
|\___ b.dns.ripn.net [ru] (194.85.252.62)
| |\___ ns3.fulinaohps.ru [fulinaohps.ru] (210.71.250.131) (cached)
| |\___ ns5.fulinaohps.ru [fulinaohps.ru] (184.106.195.200) *
| |\___ ns2.fulinaohps.ru [fulinaohps.ru] (110.164.58.250) (cached)
| |\___ ns1.fulinaohps.ru [fulinaohps.ru] (41.168.5.140) (cached)
| \___ ns4.fulinaohps.ru [fulinaohps.ru] (203.171.234.53) (cached)
: :
Tracing to emmmhhh.ru[a] via a.root-servers.net., maximum of 1 retries
a.root-servers.net. (198.41.0.4)
|\___ a.dns.ripn.net [ru] (2001:0678:0017:0000:0193:0232:0128:0006) Not queried
|\___ a.dns.ripn.net [ru] (193.232.128.6)
| |\___ ns5.emmmhhh.ru [emmmhhh.ru] (184.106.195.200) *
| |\___ ns2.emmmhhh.ru [emmmhhh.ru] (110.164.58.250) Got authoritative answer
| |\___ ns1.emmmhhh.ru [emmmhhh.ru] (41.168.5.140) Got authoritative answer
| |\___ ns4.emmmhhh.ru [emmmhhh.ru] (203.171.234.53) Got authoritative answer
| \___ ns3.emmmhhh.ru [emmmhhh.ru] (210.71.250.131) Got authoritative answer
|\___ f.dns.ripn.net [ru] (2001:0678:0014:0000:0193:0232:0156:0017) Not queried
|\___ f.dns.ripn.net [ru] (193.232.156.17)
| |\___ ns4.emmmhhh.ru [emmmhhh.ru] (203.171.234.53) (cached)
| |\___ ns2.emmmhhh.ru [emmmhhh.ru] (110.164.58.250) (cached)
| |\___ ns5.emmmhhh.ru [emmmhhh.ru] (184.106.195.200) *
| |\___ ns1.emmmhhh.ru [emmmhhh.ru] (41.168.5.140) (cached)
| \___ ns3.emmmhhh.ru [emmmhhh.ru] (210.71.250.131) (cached)
: :
Tracing to errriiiijjjj.ru[a] via a.root-servers.net., maximum of 1 retries
a.root-servers.net. (198.41.0.4)
|\___ b.dns.ripn.net [ru] (2001:0678:0016:0000:0194:0085:0252:0062) Not queried
|\___ b.dns.ripn.net [ru] (194.85.252.62)
| |\___ ns4.errriiiijjjj.ru [errriiiijjjj.ru] (203.171.234.53) Got authoritative answer
| |\___ ns2.errriiiijjjj.ru [errriiiijjjj.ru] (110.164.58.250) Got authoritative answer
| |\___ ns3.errriiiijjjj.ru [errriiiijjjj.ru] (210.71.250.131) Got authoritative answer
| |\___ ns5.errriiiijjjj.ru [errriiiijjjj.ru] (184.106.195.200) *
| \___ ns1.errriiiijjjj.ru [errriiiijjjj.ru] (41.168.5.140) Got authoritative answer
|\___ e.dns.ripn.net [ru] (2001:0678:0015:0000:0193:0232:0142:0017) Not queried
|\___ e.dns.ripn.net [ru] (193.232.142.17)
| |\___ ns2.errriiiijjjj.ru [errriiiijjjj.ru] (110.164.58.250) (cached)
| |\___ ns4.errriiiijjjj.ru [errriiiijjjj.ru] (203.171.234.53) (cached)
| |\___ ns5.errriiiijjjj.ru [errriiiijjjj.ru] (184.106.195.200) *
| |\___ ns1.errriiiijjjj.ru [errriiiijjjj.ru] (41.168.5.140) (cached)
| \___ ns3.errriiiijjjj.ru [errriiiijjjj.ru] (210.71.250.131) (cached)
: :
Tracing to ejjiipprr.ru[a] via a.root-servers.net., maximum of 1 retries
a.root-servers.net. (198.41.0.4)
|\___ d.dns.ripn.net [ru] (2001:0678:0018:0000:0194:0190:0124:0017) Not queried
|\___ d.dns.ripn.net [ru] (194.190.124.17)
| |\___ ns3.ejjiipprr.ru [ejjiipprr.ru] (210.71.250.131) Got authoritative answer
| |\___ ns1.ejjiipprr.ru [ejjiipprr.ru] (41.168.5.140) Got authoritative answer
| |\___ ns2.ejjiipprr.ru [ejjiipprr.ru] (110.164.58.250) Got authoritative answer
| \___ ns4.ejjiipprr.ru [ejjiipprr.ru] (203.171.234.53) Got authoritative answer
|\___ f.dns.ripn.net [ru] (2001:0678:0014:0000:0193:0232:0156:0017) Not queried
|\___ f.dns.ripn.net [ru] (193.232.156.17)
| |\___ ns3.ejjiipprr.ru [ejjiipprr.ru] (210.71.250.131) (cached)
| |\___ ns4.ejjiipprr.ru [ejjiipprr.ru] (203.171.234.53) (cached)
| |\___ ns1.ejjiipprr.ru [ejjiipprr.ru] (41.168.5.140) (cached)
| \___ ns2.ejjiipprr.ru [ejjiipprr.ru] (110.164.58.250) (cached)
: :
Tracing to eiiiioovvv.ru[a] via a.root-servers.net., maximum of 1 retries
a.root-servers.net. (198.41.0.4)
|\___ e.dns.ripn.net [ru] (2001:0678:0015:0000:0193:0232:0142:0017) Not queried
|\___ e.dns.ripn.net [ru] (193.232.142.17)
| |\___ ns2.eiiiioovvv.ru [eiiiioovvv.ru] (110.164.58.250) Got authoritative answer
| |\___ ns3.eiiiioovvv.ru [eiiiioovvv.ru] (210.71.250.131) Got authoritative answer
| |\___ ns4.eiiiioovvv.ru [eiiiioovvv.ru] (203.171.234.53) Got authoritative answer
| \___ ns1.eiiiioovvv.ru [eiiiioovvv.ru] (41.168.5.140) Got authoritative answer
|\___ f.dns.ripn.net [ru] (2001:0678:0014:0000:0193:0232:0156:0017) Not queried
|\___ f.dns.ripn.net [ru] (193.232.156.17)
| |\___ ns4.eiiiioovvv.ru [eiiiioovvv.ru] (203.171.234.53) (cached)
| |\___ ns1.eiiiioovvv.ru [eiiiioovvv.ru] (41.168.5.140) (cached)
| |\___ ns2.eiiiioovvv.ru [eiiiioovvv.ru] (110.164.58.250) (cached)
| \___ ns3.eiiiioovvv.ru [eiiiioovvv.ru] (210.71.250.131) (cached)
: :
Tracing to finalions.ru[a] via a.root-servers.net., maximum of 1 retries
a.root-servers.net. (198.41.0.4)
|\___ d.dns.ripn.net [ru] (2001:0678:0018:0000:0194:0190:0124:0017) Not queried
|\___ d.dns.ripn.net [ru] (194.190.124.17)
| |\___ ns4.finalions.ru [finalions.ru] (203.171.234.53) Got authoritative answer
| |\___ ns2.finalions.ru [finalions.ru] (110.164.58.250) Got authoritative answer
| |\___ ns1.finalions.ru [finalions.ru] (41.168.5.140) Got authoritative answer
| |\___ ns3.finalions.ru [finalions.ru] (210.71.250.131) Got authoritative answer
| \___ ns5.finalions.ru [finalions.ru] (184.106.195.200) *
|\___ e.dns.ripn.net [ru] (2001:0678:0015:0000:0193:0232:0142:0017) Not queried
|\___ e.dns.ripn.net [ru] (193.232.142.17)
| |\___ ns2.finalions.ru [finalions.ru] (110.164.58.250) (cached)
| |\___ ns1.finalions.ru [finalions.ru] (41.168.5.140) (cached)
| |\___ ns3.finalions.ru [finalions.ru] (210.71.250.131) (cached)
| |\___ ns5.finalions.ru [finalions.ru] (184.106.195.200) *
| \___ ns4.finalions.ru [finalions.ru] (203.171.234.53) (cached)
: :




and so on..
(c)MalwareMustDie, the NPO - malicious domain monitoring scheme..
UPDATE: 2013, March 01
Latest domains used by this Bad Actor: 
This group is continuing their criminal operation under NAUNET(Russia) rogue registrar,
registering & activated malicious domains with rogue registration (see marked words below)
registrar: NAUNET-REG-RIPNThey are keep on updating domains for their crime operation in daily basis,
state: "REGISTERED, DELEGATED, UNVERIFIED"
person: "Private Person"
as per pasted evidence here -->>[HERE] ←see the "Last updated" part (=today)
We marked NAUNET(RU) as a wellknown malware affiliate registrar.
They are starting new infection campaign with the new M.O. as per below details:
#MalwareMustDie, the NPO, Feb 2013.Details
New infection methods implemented:1. Using the (suspected Geo-base)IP rotator base response to infection
2. Starting the infection of the Ransomware for the certain GeoIP.
3. The usage of fake/stolen CA certification is spotted. (thank's to @it4sec)
We monitored this activities for last 4days and exposed 2 reports of this case in
the our beloved Pastebin with the links below:
With the PluginDetect exposed as per below:1. http://pastebin.com/CpRXS5m3
2. http://pastebin.com/MkYVRz4R
3. http://pastebin.com/mCJy7GEn
4. http://pastebin.com/LSUCnvN6
And the "latest" Payloads as per below:
Cridex:1. 6cd8ae852bd023982b292a714d3e1582537606cc655a74c1fef152742c215e00
2. 5050a5bdf164767ba6a8432a273942983737b3553c2f0d8fdbab42bbdaab3f6e
3. a54c2b298c3fc8162458889f290d2e6713a6ba45c8c697e17a333409c037bff4
4. 6ba7598df3a3111c4304f2c565ecc8307ecef504e0413c230e87ff6d845076da
Ransomer:1. 3cb0a852b902c1beffa70e6405825dfe71ad28141f8bcc369880af9f7e692b84
2. bea956049c02eefa07495dda55a1624ba3fe4020ed268094f7b63ec53439d48d
You'll see the LATEST popped up snapshot of download binary here:
This criminal group is aiming the:1. Internet service login credentials (ftp/pop3/imap/http)
2. Online cash/transaction information
3. Phishing & fraudulence of online bankingProof of Concept
First PoC is as per pasted stealer config file here -->>[HERE]
For the security purpose we can not report the Ransomer parts yet,
but Credential Stealer Trojan used(Cridex+Fareit) are using callbacks with
the below details:
The below communication HTTP headers..(info for filtration purpose)Callback IPs..
Method : HTTP/1.1 POST
user-agent : Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US)
contents-type: application/x-www-form-urlencodedh00p://203.171.234.53:8080 // the url will be plus /XXX(random)/XXX(random)/XXX(random)Credential stealed with below POSTED formats: (note: grabbed ftp/http/pop3/internet explorer/firefox/macromedia used)
h00p://221.143.48.6:8080
h00p://64.85.53.168:8080
h00p://180.235.150.72:8080
h00p://213.214.74.5:8080
h00p://210.56.23.100:8080
h00p://173.201.177.77:8080
h00p://184.106.195.200:8080
h00p://199.167.29.136:8080
h00p://62.28.244.251:8080
h00p://85.94.66.2:8080
h00p://72.251.206.90:8080
h00p://188.132.213.178:8080
h00p://78.28.120.32:8080
h00p://88.119.156.20:8080
h00p://188.117.44.241:8080
h00p://217.65.100.41:8080
h00p://37.122.209.102:8080
h00p://195.191.22.90:8080
h00p://195.191.22.40:8080
h00p://195.191.22.97:8080
h00p://195.191.22.37:8080
h00p://82.100.228.130:8080<http time="%%%uu">Supporting the stealing method/commands:
<url><![CDATA[%%.%us]]></url>
<useragent><![CDATA[%%.%us]]></useragent>
<data><![CDATA[]]></data>
</http>
<httpshot time="%%%uu">
<url><![CDATA[%%.%us]]></url>
<data><![CDATA[]]></data>
</httpshot>
<ftp time="%%%uu">
<server><![CDATA[%%u.%%u.%%u.%%u:%%u]]></server>
<user><![CDATA[%%.%us]]></user>
<pass><![CDATA[]]></pass>
</ftp>
<pop3 time="%%%uu">
<server><![CDATA[%%u.%%u.%%u.%%u:%%u]]></server>
<user><![CDATA[%%.%us]]></user>
<pass><![CDATA[]]></pass></pop3>
<cmd id="%u">%u</cmd>
<cert time="%u">
<pass><![CDATA[]]></pass>
<data><![CDATA[]]></data>
</cert>
<ie time="%u"><data><![CDATA[]]></data></ie> // Internet Explorer....
<ff time="%u"><data><![CDATA[]]></data></ff> // firefox...
<mm time="%u"><data><![CDATA[]]></data></mm> // Macromedia....
<message set_hash="%%.%us" req_set="%%%%u" req_upd="%%%%u">
<header><unique>%%.%us</unique><version>%%u</version><system>%%u</system><network>%%u</network></header>
<data>
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDa1gmnqfz0x8rbd5d78HJCgdSgkQy7k8IISlrVm8zezmXmqtbnNt7Mtk0BZxCq0xnjc+WGc1Zd8XHAkC5smrgFLgZYMhClUOEAfDLQhsnrWyjT5spwnkEgIVOv6oifW7rPPOCGbCYi1vnDiHJdy5AQqLfl4ynb5Pk259NwsjX0wQIDAQAB
</data>
</message>hashAlso supporting the file-sending method:
httpshots
formgrabber
httpinjectsHTTP/1.1 200 OKWith sending information to the remote malicious servers/panels below:
Connection: close
Content-Type: text/html
Content-Disposition: attachment; filename=%Sh00p://37.139.47.124:80IMPORTANT! The GeoIP scheme used to rotate request is matched with the below :
h00p://85.143.166.72:443
h00p://62.76.177.123:80/if_Career/(admin.php)Research Materials
Samples Collected -->>[HERE]We recorded PCAP up to 1700+ sec of a last infection-->>[HERE]Just block this now: 84.23.66.74195.210.47.208210.71.250.131 < new IP for: emmmhhh.ru | errriiiijjjj.ru | ejjiipprr.ru | eiiiioovvv.ru
— Malware Crusaders (@MalwareMustDie) February 20, 2013Additional: Thu Feb 21 18:33:41 JST 2013 The PWS Stealer (Cridex drops Fareit) distributed via BHEK, VT: 6ba7598df3a3111c4304f2c565ecc8307ecef504e0413c230e87ff6d845076daLanding page: h00p://faneroomk.ru:8080/forum/links/column.php IP: 77.120.103.221, 84.23.66.74, 210.71.250.131 Landing page + PDF infector PoC http://urlquery.net/report.php?id=1057467Payload Url: h00p://faneroomk.ru:8080/forum/links/column.php?gf=30:1n:1i:1i:33&re=2v:1k:1m:32:33:1k:1k:31:1j Payload PoC: http://urlquery.net/report.php?id=1057662*) thanks to @PhysicalDrive0 for landing page urlquery info.The below crusaders is supporting this investigation: @Hulk_Crusader. @it4sec, @RazorEQX, @unixfreaxjp, @PhysicalDrive0
 RSS Feed
RSS Feed Twitter
Twitter 03:20
03:20
 nam tóc xù
nam tóc xù


0 nhận xét:
Đăng nhận xét