Background
If you see the post's title well, this post is as per it is. A shocky, and took us a long time to confirm the source code one by one until we are pretty sure that the data is valid.
The data was found by our team member (thank's for the great and swift follow) after receiving an anonymous hint, it was found a torrent account which lead to a file-share contains these malicious contents. The account is under legal process to the authority and we grabbed all of the data as evidence, shortly after we retrieved the data and some "one on one" battle, the account was closed and the file shared was suddenly deleted.
The malware source is a bit old, mostly are data from 3-4years ago, most of them are bots/botnet clients source codes of various malicious implementation and some of them are still considered a "useable" stuff. After having a long internal discussion, we decided to full-disclose the information for sharing purpose to the AV/security industry, authority and known researchers only, sorry for the inconveniences that might occurred, please contact us for the sample request together with your introduction (as a good guys with credential *smile*). Upon the approved requests, we don't provide the downloads URL for you, we will push via FTP for the specific sources requested (the reason is: big size & security purpose) so please prepare your temporary FTP/FTPS account. I mean FTP, means no Dropbox, no Google Drive, no File Sharing, and please no argue about this, since we have our own security reason. In some cases we will demand the PGP/GPG keys for validation.
Below is the category (supported to PHP, UNIX & Windows native C codes):
Login Brute Forcer Bot
IRC Bot
WebShell
SqlInject Attack Bot
Virus/Malware Botnet Client
Spyware/Backdoor Bot
Snapshot
Some dangerous bots (snipped in picture):
Ransomware:

UNIX Bot (Client):

Sql Brutter Client:

IRC Worm:

ZeuS:

Hashes
The complete list of the sample:
DATESTAMP TIME MD5 SIZE FILENAME
------------------------------------------------------------------------------------------------------------------
2009/06/12 19:28 f3c4064ffc78852d07c4cb3f6b23f159 438,881 (rbot)x0n3-Satan-v1.0-Priv8-By-CorryL{x0n3-h4ck}.rar
2009/06/12 19:29 6c156b3e3fe269385076880bce7fc094 2,591,697 120 Moded By t0nixx.rar
2009/06/12 19:30 276717078dda96ddd1fa7da10bdaed99 1,861,648 120-MYSQL-V2.rar
2009/06/12 19:30 fda4772759e01da0ea6e3fbd29c5dddb 1,834,838 120-MYSQL-V999.rar
2009/06/12 19:29 49a53e3490283199c43c38d7833e36ad 1,598,898 120-MYSQL1THREAD-V2.rar
2009/06/12 19:30 3bfd0b7d99b578ac9262ed5c737a230c 1,846,551 120-MYSQLBRUTE-V2.rar
2009/06/12 19:30 eccbec0caf7be85f513b37a290ffbe06 311,471 120-PSTORE-MSSQL-SYM-NTPASS-VNC-NETAPI-2007.rar
2009/06/12 19:30 9888a260793b4cc1ce42e2238b94edc7 1,629,967 120-VnC-Brute+pStore.rar
2009/06/12 19:28 f025eae0375ff22154c6972fb60adfcf 159,305 120-[BruteTest]-V0.5.rar
2009/06/12 19:28 56ef53170406d8ea82154a1d1a65b964 329,645 120-[DVNC-TEST]-DDOS-V1.0.rar
2009/06/12 19:28 6c6aba1e5af4c3d6d558d6871e02118d 233,800 120-[ModBot]-SNIFF-VNCBRUTE-SP2FIX-NICK.rar
2009/06/12 19:28 13c08d0b13b3e75bf8f6ddbfb1e43ceb 243,298 120-[ModBot]-SP2FIX-SYM-VNCBRUTE.rar
2009/06/12 19:28 70da6fc1586ac3cd0a025ea0e6aad31a 146,865 120-[ModBot]-V0.5.rar
2009/06/12 19:28 ea6fc0ea066d3e835ef28a1c90949660 312,882 120-[ModBot]-V1.0.rar
2009/06/12 19:28 5b6c4675e1616e51da2bfdc6213148f7 265,415 120-[ModBot]-VNCBRUTE-MSSQL-2007.rar
2009/06/12 19:28 74fd34fc2b497602237402bbaedba8a2 240,382 120-[netapi-sym-mohaa]-(vncbrute-sp2patch).rar
2009/06/12 19:29 ad693fb4e2313fdc78b883c417f8ad3a 207,623 120-[SP2-PATCH-BRUTE]-V2.0.rar
2009/06/12 19:29 342aefc091d1e82cb8813e7bba535dda 196,201 120-[SP2-PATCH]-V2.0.rar
2009/06/12 19:28 4800ee7bc8a9e3f4d8a4f82722f02c42 228,752 120-[SP2FIX-VNCBrute-Mohaa]-STRIP V1.0.rar
2009/06/12 19:28 24ff016f81aa71a20df1226255960f12 240,027 120-[SP2FIX-VNCBrute-Mohaa]-Test V1.0.rar
2009/06/12 19:28 cac14cb51f4ece12a357759ac82df8dc 227,567 120-[SP2fix-VncBrute]-FINALV1.0.rar
2009/06/12 19:28 68c45a875dba68c638e1cb8d139d118a 283,206 @@ SKUZ FIXED DDOS @@.rar
2009/06/12 19:30 a05ef342a2d0059a6ef895a18d43922c 514,428 a.rar
2009/06/12 19:30 eef69909a5e0598b1045f16771e316dd 991,860 a59base.rar
2009/06/12 19:30 64f9e1ae1e6a578ffee4b9fb32868d45 8,460 acidBot.rar
2009/06/12 19:30 52670ac6c7bb1f7e971b0b6c7f28b146 10,821 acidBot2fix.rar
2009/06/12 19:30 9f8dc19511a188e8fdbd3f454d92df60 6,224 acidbotEncypt.rar
2009/06/12 19:30 1530eb627c220286792abbf0658c5b7a 7,841 Ad Clicker Bot - Private - Free-Hack VIP Tool.rar
2009/06/12 19:30 90a02f5853087a9f08ed4fddada1f81e 1,470,160 agobot3-0.2.1-pre4-priv.rar
2009/06/12 19:30 17488ed87161e959bf9ea1f25d206d78 66,405 AkBot-IRC--lsd-mod.rar
2009/06/12 19:30 9842020705382d29a3c3bc23dd2103f7 90,263 AkBot-x0r-dns.rar
2009/06/12 19:30 5c4e92b534053bb0217199ec7d85bc24 168,342 Akbot_v0.4.1_netapi_.rar
2009/06/12 19:30 20635cea0f079ca7cd4395da99f05a62 142,885 asn-pstore-spam.rar
2009/06/12 19:30 ed9f49a1bb5bf552c34fc5b8d942269b 141,693 aspergillus_1.3.rar
2009/06/12 19:30 9030d27bf842ff8233752724e10c7c81 402,767 bBot-Version_0.6.rar
2009/06/12 19:30 de08fa387c1148568104d61d7b8ae609 17,502 BioZombie 1.5 Beta.rar
2009/06/12 19:30 7a232e2c7ef0085d0fa1c4eb859d20d8 112,302 blacksun.rar
2009/06/12 19:31 99d56b1460686e0da2a1e1586cb021cd 278,984 BlowSXT.rar
2009/06/12 19:31 1fb2d733cf36e9d352dbb999fba0ea2c 60,462 bmw.rar
2009/06/12 19:31 1cf0cd89a05814fadddc835934226bb3 43,176 bot mods.rar
2009/06/12 19:31 2b36670d863e7a89586c6137a8f30d82 269,740 botnet200.zip
2009/06/12 19:31 e1dc44e0de020ecd29e5c1a0eaa93a8d 3,270 Brainbot_v1.5.zip
2009/06/12 19:31 fe7f5c930537a25c676c317f0f7ede55 185,794 CBot-Fixed Version.rar
2009/06/12 19:31 59a95e39a104798872084ab1954e42f1 2,119,050 ChodeBot C++ v1 base.rar
2009/06/12 19:31 54d994b223b34aa3793dac250f69ecb7 197,682 ciscobawt.rar
2009/06/12 19:32 7416e613bd89dc18876ee54054e2e28e 645,293 Crackbot_v1.4b-final_spin.zip
2009/06/12 19:31 e41507022a1c46d4667586150d6bff2e 192,638 Crx-realmbot.VNC+RFI.rar
2009/06/12 19:31 b38bdca4ae6d993258ff7b341ef641d3 197,107 Crx-realmbot_VNC_exploit.rar
2009/06/12 19:31 d826b47ee22d43edcc3e91213d7a6fa1 131,999 CYBERBOTv2.2-Stable.m0dd_ownz.DreamWoRK.rar
2009/06/12 19:31 b4bd7566c8f52504def1520daa619f10 89,904 CYBERBOTv4.0.rar
2009/06/12 19:31 b01e2800778e0356a7125d0b169016cb 19,352 C_15Pub pre4.c.rar
2009/06/12 19:31 aef6eeec9dab3614040924a42bc1e59a 26,398 C_15Pub.rar
2009/06/12 19:31 00c39caedea5396e5ef752c7124b6478 209,817 DarkAnalNKX-BACKDOOR-REMOVED.rar
2009/06/12 19:31 0cc93898910b2e28d11bcd6015df2d95 514,997 Darkness IRC Bot.rar
2009/06/12 19:31 4c736cb10035c4c1d938dd56a9392e73 470,970 Darkness.last.mod.rar
2009/06/12 19:31 613e31fde44dfb58bc5827382a6d2121 116,307 dbot-irc-sell.rar
2009/06/12 19:31 f47bde579b059da5d2100dc3d57addb6 67,747 Dbot.v3.1.rar
2009/06/12 19:32 c3c889b923b47f051b6aec0dac9c6b9b 2,676,329 DCI Bot.rar
2009/06/12 19:32 4f7e093d42e53daba32eb4be642ceab6 817,799 dci_bot.rar
2009/06/12 19:32 28088545580766d59a5980bb166262ab 100,233 dopebot.rar
2009/06/12 19:32 bc487a321f966901ccff083fdfb9d76d 1,159,465 dopebot0.22.rar
2009/06/12 19:32 bc487a321f966901ccff083fdfb9d76d 1,159,465 dopebot0.22.uncrippled.rar
2009/06/12 19:32 53bf7302b4d1652f82d66f810d8ee941 107,161 dopebot_2.0.rar
2009/06/12 19:32 64e29da4acd67784ac7902a8a7d5778e 128,622 dopebot_current.rar
2009/06/12 19:32 9f888ff2dff506e1275857865f8273ba 251,418 drx_realcast_woopie.rar
2009/06/12 19:33 a34bbb6b2ab99869ca9ce040954e1a54 1,113,713 fiesta Sploit-pack.rar
2009/06/12 19:33 2809919d7df5c98fb8d72179759b1271 2,776,404 ForBot_Olin-SYM-VNC-NETAPI-All_The_Public_Shit.rar
2009/06/12 19:33 1a5a554cf0d51a946bb39b41afb127d7 691,904 ForBot____sniffer__other_mods-_ch405_.rar
2009/06/12 19:33 94569dfd1e3c39b0887b15602d1282b4 910,480 frozenbot6.rar
2009/06/12 19:33 be9041ce8838fd8cc3fa19c9231307b4 218,854 fukj00.rar
2009/06/12 19:33 dc163d64564178a5228be6904e1a1afc 74,862 fungus.rar
2009/06/12 19:33 8f237784ce29a851a2c10e091bc7647f 1,365 fxBot_beta_.rar
2009/06/12 19:33 99013df00a00db8377a37edf96f43710 450,355 g-spotv2.0.rar
2009/06/12 19:33 cce327ac783ed2e03f3804a4711b2980 98,338 Gellbot_3.rar
2009/06/12 19:34 9f62032cec5bf5a6829f8f8ed62b4740 943,873 GENTOOreptile-base.rar
2009/06/12 19:33 e0e204b89ee612879184473714aea2f5 405,270 GigaBot-DCASS.rar
2009/06/12 19:33 e35b3b428bae342f9e9b5c416a444111 20,944 gsys3_final.zip
2009/06/12 19:34 1bcc13ffc13a60b61cc20de05323f78c 477,851 gt-badteam.rar
2009/06/12 19:34 7c9081af12474e58bf877e04f1fb6173 639,102 gt-virtualslut.rar
2009/06/12 19:34 f508da5fe53f643838b07bdb31f6173a 631,223 gt.zip
2009/06/12 19:33 a56fa0c5bc1f9adfcdbf10af4e40e958 18,085 gtbot-hackersteam.zip
2009/06/12 19:34 c216d6757a0a944881fa1038dc105a69 61,125 gtsev-spreader.rar
2009/06/12 19:34 c216d6757a0a944881fa1038dc105a69 61,125 gtsev-spreader_2_.rar
2009/06/12 19:34 4ba2a256f576f49fa6ddcc8b3ca850d3 461,610 H-Bot M0d 3.0 M0dd3d by TH & Sculay.rar
2009/06/12 19:34 4a242f6d83c001d6737ac1b743005784 582,435 H-Bot_M0d_3.0_M0dd3d_by_TH___Sculay.rar
2009/06/12 19:34 dc958fff0f8538c6cb1a1816b16b2586 16,116 h3xb0t.rar
2009/06/12 19:34 bc0d89415675a722f2af74b0c174ad29 28,672 h4x0rb0t_2.0_gt_edition.zip
2009/06/12 19:34 2ba073919798b49fda385298fe64d935 1,198,546 harvecter_bot.rar
2009/06/12 19:34 131e297fcb7b4097327352b11c078982 94,865 hdbotv0.2-ciscoscan.rar
2009/06/12 19:34 115881fb06d2ab57abf8afb7f4ae1815 88,956 hellbot10-06-05.rar
2009/06/12 19:34 3acba4c7f32087368937d7b4fdc29038 62,560 hellbot3[10-06-05].rar
2009/06/12 19:34 19b1ea7eb040789fa35d4e31909da225 90,126 hellbotv3.rar
2009/06/12 19:34 e1688beaf7b28f279abb90da00faeee8 16,905 hydra-2008.1.zip
2009/06/12 19:34 40a3282cf7e1d832ddfb4e6c33fc0252 17,443 I1.4b0.rar
2009/06/12 19:35 e09d194f790134f500c4c30aa0ff2388 1,231,092 icepack-ie7 mod.rar
2009/06/12 19:34 9d08ed0af3b70cd4fa0858698071c7d6 199,267 IHS-H-A-V003-Exploits.zip
2009/06/12 19:34 e23d9fde0bb6c1d84344bb291ad6afb3 495,581 iis-gt-bot.rar
2009/06/12 19:34 b7bb59167431b696a400c076b83ca22c 224,062 illusion_bot.rar
2009/06/12 19:34 3434dd0e03e545c647d0026d57dbb83b 248,553 Imbot1.3_V3.1.zip
2009/06/16 01:31 9d7f2f4c776062f7eb1300142bb44f6b 80,290 IMbotMod_V4.1.zip
2009/06/12 19:34 299ad5de20ba8c3c9182fdcb33016bc6 207,505 IMBOT_MOD.rar
2009/06/12 19:34 8493cbdc1fcb1caf3f32b9a8a548b179 97,313 IMBot_SRC_$$.rar
2009/06/12 19:34 eba95d73077c762dfd5c05fd871db38a 170,393 InTeL_m0dd-Test101-ms0640.rar
2009/06/12 19:34 2968af1c1a9ca3c1b8258f5902ec91c6 105,750 irbot0.15.rar
2009/06/15 20:15 ce35769c0538f13f599dcc5c0b6d9e96 2,555,449 ircd.tar.gz
2009/06/12 19:35 8e4c53d9673e44ff9df410288c5f0050 34,728 IrcWormv1.3-SourceCode.zip
2009/06/12 19:35 c52acf3396793f97bda614252bd8492d 1,991,254 IrINi_bot_0.1_public_limited_version_for_win32.rar
2009/06/12 19:35 63e0c87e11fd8e46111a5e734975d9f0 662,071 italian.zip
2009/06/12 19:35 ae71290e63db49bdda0ae0b0b8bfe88f 296,592 JRBOT_Modded_By__bloody_.rar
2009/06/12 19:35 3f7cf217ec499ba9d34e86e47cf08efe 8,643 kaiten.c.rar
2009/06/12 19:35 8dd36535dc8af32d6f398706b7f63c3e 7,322 knight.rar
2009/06/12 19:35 e44a741b6507ad9bb14c1ccd152a48ed 5,586 KoBRA-RFISCaN.EDiTEDBYBRaT.rar
2009/06/12 19:35 6cee5d68699c496c59afa6d9aeb2c75b 11,201 l0lw0rm.rar
2009/06/12 19:35 7f0657b3fb5ec9b67ce2487a8040ca05 227,961 LiquidBot_FixEd_By_Pr1muZ_anD_Ic3.rar
2009/06/12 19:35 4e8a71749ece0c3209f40c0304d1c7e2 86,201 litmus2-bot.rar
2009/06/12 19:35 4e8a71749ece0c3209f40c0304d1c7e2 86,201 litmus2-bot_2_.rar
2009/06/12 19:35 d43da1e84969c2eb0ba1ef760681e671 2,751 Lnknell.rar
2009/06/12 19:36 cbdbc295c611f1b1c6dcf11da45e4878 2,028,539 LoexBot.rar
2009/06/12 19:35 db5420ab2a883ed938aae77429573135 128,635 M0LdBotv1.0-small.rar
2009/06/12 19:35 9d90100354b9efeae6fc3f57ab0a036d 249,373 mm0d_asn_.rar
2009/06/12 19:35 9d90100354b9efeae6fc3f57ab0a036d 249,373 mmodbasn.rar
2009/06/12 19:35 f8bede07136fb166a0b4d197a24c7723 327,656 ModBot V1 Mod by iNs v0.2.rar
2009/06/12 19:36 1b521746de9dc8c77658d5bf9ed46786 1,387,852 MSDN(mirc scan bot).rar
2009/06/12 19:35 4ba39b27d1976eabc28cd71e515fac82 33,627 MSITBotWin.rar
2009/06/12 19:35 45b6ce6fef7e3e2d5769a3c2a1979daf 45,149 MSN Spread Bot Priv8.rar
2009/06/12 19:36 003a33c8e9701722179c99980bfdbfac 247,232 mystic-Urx.rar
2009/06/12 19:36 2d7328e87f0570a3bbd2ebdf76183cc7 240,673 mystic-Urx_Fixed_by_Pr1muz.rar
2009/06/12 19:36 88eac4e54021a2cf0ca8137f35b21bc2 647,269 my_poly_sploit ie6-ie7-op-firefox.rar
2009/06/12 19:36 8e4c63ff630c591d36dcb64dd7e1c15b 116,659 Nbot.rar
2009/06/12 19:36 3d0e097817ebd904fecd4645b8186b14 110,060 nbot032-update-5-28-08-enc_07-10am_.rar
2009/06/12 19:36 2d1927aa1a0a05d9e6ed1f8a4bc83579 213,512 NESBOT_v5.rar
2009/06/12 19:36 cb6e2ab433ddd93acc92b8127c408168 149,543 nesebot1.1r-ASN-PNP.rar
2009/06/12 19:36 ea9433508e84ece9647389999491a472 206,253 nesebot1.2.rar
2009/06/12 19:36 4bd17a046c2c34cd65210f386af85cb8 252,529 Netapi.Prueb-Norman.2oo6.Prif-Jessi-Off.rar
2009/06/12 19:36 4f1a198048010bebe6a496c2b6482756 211,737 New Folder.rar
2009/06/12 19:36 4d691657be055879d7961a5ccf845f1b 232,021 New_NZM_netapi_bot.rar
2009/06/12 19:36 1650de57781e5e2145c4aeebdc5c6ad5 14,946 niggerbot-vnc-nocrypt.rar
2009/06/12 19:36 8fc87d29d7ac4933c61a2c73df3174e8 94,040 NinjaBot.rar
2009/06/12 19:36 53ad266492c5ac6a166c2281e6bd2130 20,208 NITE-AIM.rar
2009/06/12 19:36 df8d52c0d08e277cc43c472dca2ed8cb 42,667 NtScan-rbot.rar
2009/06/12 19:36 96691ea655bf3dee6101a4af666d99b9 112,504 nullbot[2.1.1] [23-11-05].rar
2009/06/12 19:36 c14512df73863f6520fc04f095f74858 112,489 nullbot[finals].rar
2009/06/16 01:31 2c1c70b4fbbd2652051f6a8e48fc9ad7 252,691 NzM 3.0 By Ph3mt.rar
2009/06/12 19:37 1b2ef2799610f4db8fab315bd269123e 866,864 nzm-netapi.rar
2009/06/12 19:36 b2c297155d283e15aaa7de677ce1c831 447,772 nzmlite_sql.rar
2009/06/12 19:36 96045f06b6fe0b10ab8876a0ee120402 221,135 nzmlite_symantec___.rar
2009/06/12 19:36 5f6ebad8d78f6a60d9b2a084e503b855 401,538 nzm_priv_shit.rar
2009/06/12 19:36 36605f658061064219b2c7364250f478 66,557 oscar.rar
2009/06/12 19:36 4ff53675ff4cdd829da9b0a42f358e81 6,948 pBot.rar
2009/06/12 19:36 54566f2c6d73bd7837a5a51bfcaf38e6 6,397 pBot_v2.rar
2009/06/16 01:31 97351e9d23d352e6aa1f2b62e55f37c2 327,680 ri0t[v5].rar
2009/06/12 19:28 787edfdfdc5610c9f4b8cfb77de93399 533,970 _dkcs_ddos_bot.rar
2009/06/12 19:28 02cd4a3f219739942fb3f74468318f99 714,852 _Radmin-scanner_-EcKstasy.rar
2009/06/12 19:28 02c1edcbc84d3e1a173a377955c43bd6 677,164 _sHk-Bot.svchost-ns-dev.NOT-FOR-RELEASE_.rar
2009/06/12 19:40 6f1965b7156d0f45702b54f1ab1dcf9b 8,330,434 Phatbot-gh3tt0Bot.rar
2009/06/12 19:38 468c6a889d70027bef6e1b36915f6c88 3,072,230 Phatbot-NortonBot.rar
2009/06/12 19:38 343890fa7a2bf1456be638419d45302d 1,940,198 phatbot-SkYKr3w.rar
2009/06/12 19:39 7139728433d292be62fe205e6a17b76a 3,348,672 Phatbot-stoney.rar
2009/06/12 19:37 85a8b554fbecc76b04d584be7e023983 1,316,528 phatbot[11-20-04][PCAP][SYNSCAN].rar
2009/06/12 19:37 e0a856cdd29f7a94d5c55ceac9b942fc 1,500,349 phatbot_alpha1.rar
2009/06/12 19:38 dcc4bc9260c9b9b45900a30b4e3758f2 5,532 phb2.rar
2009/06/12 19:38 afc6284bb1e5ea18897c77708c6a7476 3,464 php_bot.rar
2009/06/12 19:38 dfa368e6624d8dc7e03a7e2c35d3e4e3 278,407 plague.gecko.netapi.rar
2009/06/12 19:38 f629aaf7d78d9020d8620407d84e0346 357,695 pr1vsrc-nzm-m0d-by-ibby.rar
2009/06/12 19:39 e6b2deed37a64d027fd537f4ecc062c3 247,327 private_enzyme_rxmod_04-04-05.rar
2009/06/12 19:39 7a76d91b3ac04e15e74e9a127553720c 257,317 prueva[1].Netapi.asn.m0dded-Norman.rar
2009/06/12 19:39 f8929c235aa51ded4f94e32cc778c4e4 247,912 prv_nzm-rx.sp2fix.rcast.rar
2009/06/12 19:47 63d5ce47604dd47e658be563606c7af8 19,031,884 PsyProxy.zip
2009/06/12 19:39 ee5de8ed6a9e8ae2fe1304222bd668a3 246,038 pwnBoT.rar
2009/06/12 19:39 fa302cd7352ad3e8420fa3ec8924f842 8,372 q8bot.zip
2009/06/12 19:39 f4ed84cdef31f7235f163d20668edf97 216,679 r00t3d.asn.ftp.lsass.by.Morgan.rar
2009/06/12 19:39 78c02f7ec3b5af667cccd7a2d3754f07 130,140 RAGEBOT.rar
2009/06/12 19:39 9a6d2a549b4ea49e3ede33b2f8957cb1 102,702 RAGEBOT[Clean].rar
2009/06/12 19:39 b946350e3f2348bf578803919ba9f65a 18,016 RansomWar.rar
2009/06/12 19:39 e61ca1f98b33e10a0f14e885ebdd2510 6,200 Ravbot.rar
2009/06/12 19:40 18dcba301450a14e3261225163991de3 28,629 rbot-LC-Priv8.rar
2009/06/12 19:41 36d130cbfd1fccb685ad42f303997a04 288,289 rBot-sxt-harro.rar
2009/06/12 19:40 20d6865263e96848754353930ffc3c74 120,044 rbot0.2-scionix-102b-working.rar
2009/06/12 19:40 88e0d9bfaf3dccc46230dc6d70495688 159,057 rBot0.3.3Pub.rar
2009/06/12 19:41 e86d83476b327e7df82d4cf43eb733b3 220,647 rBotv0.6.6-privlsass.rar
2009/06/12 19:40 839e1825a9580a03032de1bbf46b6059 1,169,550 rBot_0.2-MODE-by-akusot.v1.5.rar
2009/06/12 19:40 72dd0e30b85f0b3e64198520afa584da 72,666 rbot_dnsquery2007.rar
2009/06/12 19:40 0441ceff1c609627e0028c066e1a519a 415,849 rbot_netapi_vnc_ipswitch.rar
2009/06/12 19:40 234a3f399969dd621c71c6add8cc2a47 66,993 rBoT_oTh3R-dImeNsIoN_4.4x(2).rar
2009/06/12 19:40 234a3f399969dd621c71c6add8cc2a47 66,993 rBoT_oTh3R-dImeNsIoN_4.4x.rar
2009/06/12 19:41 62bc8519bf3eb573c58f23494b36ab00 247,426 Release no_cpp.rar
2009/06/12 19:41 2f4327515aff4a16196e460d55658382 317,296 reptile-small.rar
2009/06/12 19:42 d6a4075a7edbf3f6a8d24eae3c13bfbe 2,458,703 reptile.04.pnp.asn.ftpd.reload.rar
2009/06/12 19:41 82e4700bbd4e81643cb9f69dbe887ede 2,428,941 reptile.rar
2009/06/12 19:41 a92d4c607a2a4877b39b9e4a5399525b 234,311 Reptile._small_.DMG.Fixes.0x1FE.rar
2009/06/12 19:41 5a0e13a825e520c785848653e1fca8f4 97,352 rezo.ninjabot.zip
2009/06/12 19:41 53e7e66ffe37fc1d96c56dbec771d9e6 317,064 RFI-SCAN.V2.PRIVATE-1x33x7.rar
2009/06/12 19:42 f0a504aa728922406552dbfddd18df23 851,993 ri0tv5.rar
2009/06/12 19:42 1530ed8db18f47c23e9b94837865c93a 760,056 ri0t].rar
2009/06/12 19:42 c8ec81bb03371c8a176cb6e2589fb8c8 158,637 ri0t_v4.rar
2009/06/12 19:42 5cb7edb4ad178fb63b5d443dbf413798 344,515 ri0t_v5_.rar
2009/06/12 19:42 15de82b050ed3def8c3c7c8c0aa9e7a0 66,789 RNM5-Priv-Pr1muZ.rar
2009/06/12 19:42 bbba5301ca57ea9337720695861a3c62 72,004 rnm5b.rar
2009/06/12 19:42 fb6afedb3ab60fb63f9902fbef710aab 107,604 Rose v1.3 2007 by DreamWoRK.rar
2009/06/12 19:42 2053825af23c7ff10027d4c0d734daa8 200,570 Rose1.1.rar
2009/06/12 19:42 869243cb22e16b96b7ec60fa8f8f5a3c 268,082 Rose_2008.rar
2009/06/12 19:42 f2d9e3b23729e9d46043c77ff962badc 145,470 Rose_v1.3_2007_by_DreamWoRK.rar
2009/06/12 19:42 3bcf15b667707be1bab0d94b5b1a7380 127,851 Ruffbot1.2-MassAsnPrivShit-150705.rar
2009/06/12 19:42 d1744451650673b13465aec4b765f22f 425,351 Ruffbotv2.rar
2009/06/12 19:42 f53ad631bbccf511b883b55d6f1bdf1b 174,378 rx-14-09-06_Netapi_doyley.rar
2009/06/12 19:43 a27f77bf36e62ecb2032f401b6ee3204 324,778 rx-AKMod___msDTC1025- Stripp3d------sc4nn3rz.rar
2009/06/12 19:43 ec2561b44a61d041c398574086785e0c 319,638 rx-asn-2-re-worked v3.rar
2009/06/12 19:43 1e67d41177165910e435287db306a5d1 323,336 rx-asn-2-re-worked_v2.rar
2009/06/12 19:43 901c4b3f29a5cb17759bfab16834e57b 333,391 rx-asn-2-re-worked_v3.rar
2009/06/12 19:45 af68b52c74732143ebc8bbdb787fe02b 1,419,782 RX-GUTTED.rar
2009/06/12 19:45 aae2f25f6a723963c71367aee9423570 197,060 rx-sky2kpnpprivate.rar
2009/06/12 19:46 c13f005a869f4e94442bfb44181c7fbc 4,976,033 RX-STRIP-BOTKILLER-0.5.rar
2009/06/12 19:44 69b427aa15549ecfe51279f7b4469cb7 257,880 rxbot-EcLiPsE cReW 1.1.priv.rar
2009/06/12 19:44 69b427aa15549ecfe51279f7b4469cb7 257,880 rxbot-EcLiPsE-cReW-1.1.priv.rar
2009/06/12 19:44 3e3aa7373a0edbfb2dabeeafa4aa6813 284,100 RxBot-MP.rar
2009/06/12 19:44 576bc25b74b1db3a326a72d106a6a2b7 142,874 RXBOT-RevengE2005pnp.rar
2009/06/12 19:44 51d41661674d19d199f1d00b34565e6a 283,581 rxBot-sxt-harro.rar
2009/06/12 19:45 182b9c39d50551e35acb9dc59e194b67 1,011,736 rxbot-xerion-2.0.rar
2009/06/12 19:43 9a9e3aaf4ffd6de3a56cf71f614676c7 266,640 rxBot0.6.6b-priv-stable-CoKeHeAd.rar
2009/06/12 19:43 fdbc9c8665f8bccd6b521e8091f57f65 302,520 rxbot2006.rar
2009/06/12 19:43 40d47769b8cbb15bf3d7511510af8695 605,643 rxbot7.5.rar
2009/06/12 19:43 90e086817c78266f9009e53085b126c6 231,691 rxbot_0.65.zip
2009/06/12 19:43 a9ba6ca3eb4f040c3c7fca1ace9515a2 217,103 Rxbot_7.6-Modded-Tr0gdor.rar
2009/06/12 19:44 a9ba6ca3eb4f040c3c7fca1ace9515a2 217,103 Rxbot_7.6-Modded-Tr0gdor_2_.rar
2009/06/12 19:43 35481b70cdcc19d97eb63cf7bc8cb8cf 179,516 Rxbot_ak_7.7_fira_pviv8.rar
2009/06/12 19:44 f907e1af2bb422836f3302f4dcf23304 130,797 rxbot_undertow-6-10-05.rar
2009/06/12 19:44 5d88290eca0ad4478d75059f5ddf0c9e 210,216 rxbot_undertow-6-6-05ASN.rar
2009/06/12 19:44 af35f62151da19b2c5d419473bef33c2 2,047,507 rxbot_undertow[PnP]modded.memcpy.0.2.rar
2009/06/12 19:44 bef073118968d7bf99b195474a2c7cee 157,149 rxbot_v0.6.5_pk__lsdigital_spreader.rar
2009/06/12 19:44 3b62b52cae6a2942ecbf34d684c7619c 227,347 rxBot_v0.7.7_Sass.rar
2009/06/12 19:43 2121a41a5b764c4ec0557b42f24b2fc7 289,581 RXB__tM__d-VNC-NETAPI-ASN-2006.rar
2009/06/12 19:42 5aa288d2a1692673803d723ad59706e0 65,533 rx_dev+service+working_lsass+sasser+ftpd.rar
2009/06/12 19:42 9273d451ebdd01b9380efea5ea42948c 474,597 rx_dev_service_working_lsass_sasser_ftpd.rar
2009/06/12 19:43 5e3fd5677376500c00484d16f473bda5 217,685 rX_lsdigital_Mod_priv.rar
2009/06/12 19:43 0e739e4b87c4ff60888d31c4baef1684 258,739 Rx_Temptation.rar
2009/06/12 19:45 d74793f5072ad764f4428f6652fb3801 7,863 s5.rar
2009/06/12 19:49 798b16d4018b74a74555938deb06d619 1,858,529 Sbot-RARSpreader.rar
2009/06/12 19:45 7f480ebe0a8bd58ef49ad6579b1986e9 64,994 SBX.amk.0x00.rar
2009/06/12 19:45 b47655beb2153f8f9d8f906786b6461e 142,660 screens.zip
2009/06/12 19:45 2117589061d5ae386e68ac140b425106 89,489 sd with fake xdcc by Synco.zip
2009/06/12 19:46 5bbcbe76a73c8e7a0392c0e41867f5a3 100,167 sdbot i3s.rar
2009/06/12 19:47 7061b41082cf46b051c0f68a735065de 50,889 sdbot-ntpass-codefix-nils-22.10.03.rar
2009/06/12 19:46 a0bab8e230cc6f2bfa963dfb84416a3a 28,930 SDbot05b-getadm.rar
2009/06/12 19:46 b16e8a33e54e5fdcf721b1653b1afe81 57,481 sdbot05b_skbot__mods_by_sketch.rar
2009/06/12 19:46 99ab1f471ec8ea0ec12a0eff605af2d9 390,300 Sdbot_Hardcore_Mod_By_StOner.zip
2009/06/12 19:46 7e027233923c53a9d33c087e6e698dff 92,181 SDBot_with_NB spreader.rar
2009/06/12 19:47 6a9abbe9db6d919e30f42fc40484c5be 51,312 SDX.amk.0x00.rar
2009/06/12 19:46 06b17aecd7f744a502f0789f88c1e4c3 402,522 sd_bot_all.zip
2009/06/12 19:47 f26b2deb2d9fc65ad74554737df53d36 3,022,716 shadowbot-m3.rar
2009/06/12 19:47 dc626ec6e103da5aa5e34c9209b93096 116,185 shadowbot.rar
2009/06/12 19:47 227204fd6958067d53765b5145641904 86,441 shadowbotv3.rar
2009/06/12 19:47 1d5a6cd11731d12dbf980f00924c3e5d 521,820 shellbotFTP.rar
2009/06/12 19:47 02c1edcbc84d3e1a173a377955c43bd6 677,164 sHk-Bot.svchost-ns-dev.NOT-FOR-RELEASE.rar
2009/06/12 19:47 d3ecb7e97103009399f03519160e1168 204,781 SkuZ-BoT-V.1-2006-.rar
2009/06/12 19:47 25f9f0c5e37a4579fcd213b330cfb692 289,319 SkuZ-Netapi-VNC-IM.rar
2009/06/12 19:47 8586b8374c955d84ac360507eb169ce5 15,518 Sky Bot_incomplete.rar
2009/06/12 19:47 6c3e198b78774f4ce202b849e1acea38 46,185 Skype_Spread(PoC).7z
2009/06/12 19:47 7062e27b7b355f396f41134f5c297587 9,806 Small.rar
2009/06/12 19:47 e5f228844bfeeddf2a2c2c6452a6f1ec 90,650 SpazBot.rar
2009/06/12 19:47 fee0531a4bb6baae558752a149828f07 333,754 SpyBot Leechbot_r1.5a_private.rar
2009/06/12 19:47 eb1e2e57a68f536f7592e985d40d6fdd 35,088 spybot1.2-FULl.rar
2009/06/12 19:47 2163ce34a63d2088dfe4af673f4f0261 95,696 spybot1.4.zip
2009/06/12 19:47 cce221fca66c9b9ed96605c9e4c57ff3 36,470 spybot_1.2c.zip
2009/06/12 19:47 80145a460f300a2a70faf397ed66ba2f 91,107 spybot_1.3m.zip
2009/06/12 19:48 c8fb061171652dbb2d518dca7dbe27e9 89,331 spybot_1.4.zip
2009/06/12 19:48 2b183360db6e212a3a6c2836f53137e2 53,537 STEAMBOT-src-2008.rar
2009/06/12 19:48 8dcdeb211ed5077d5dfd85168992ae5b 385,550 Stripped-RXV8.rar
2009/06/12 19:48 5b11513082401b1231e17a4a7777a0c3 22,071 svBot_.rar
2009/06/12 19:48 e7714da35836571a071e83e90115a572 24,742 svbot_activex.rar
2009/06/12 19:48 e05085b6362f3f9cbb9f281c7db08033 313,360 svmail.rar
2009/06/12 19:48 de29ce28b985c781b64357bfd7c4d5c9 180,780 SYM-VNC-NETAP__304_-ASN.rar
2009/06/12 19:48 12a4ccecca84db4909b477468c478594 291,529 TANKBOT 1.0.rar
2009/06/12 19:48 1f0f78be8fe1596680041495783ea08d 37,318 tgspy_nt.zip
2009/06/12 19:48 ad19cf692eb1dd180b12ad546e5e75c9 1,479,024 TsGh_Bot_v3.rar
2009/06/12 19:48 e3c6ead12b4ed521dd2bcfa127b489cf 250,381 uber-wks-asn-m0dded-Pr1v.rar
2009/06/12 19:48 28ccec60a3da99fcb2f3221167c13586 83,202 Unix bot 2.2.5.rar
2009/06/12 19:48 64409a5e2ca611ccc826947654923335 127,945 uNk + USB.zip
2009/06/12 19:48 bd2138b06d33df22e83ffda0bc210f71 203,100 URX-pnp-asn.rar
2009/06/12 19:48 eb14beaa111df581ff7b4a30e3b9fdfd 176,144 Urx.SYM+ASN.rar
2009/06/12 19:48 620bd3c7138c838140ad0cb9aaa760e9 253,664 Urxbot.pRiV-sKull.MoD-ASN_FTP_WORKING.rar
2009/06/12 19:48 a3d68eeff0dc4ee2c58a090c49464685 25,987 vbbot.zip
2009/06/12 19:48 a8f635399ab05d197237e5c6c452ba1b 49,639 vBot.rar
2009/06/12 19:49 164f47d80a5f4b2b103e633c9e69b32a 701,859 VNCscanner.rar
2009/06/12 19:48 89da2d3dbe384977dce0503c10ba5a39 250,208 VrX-5_Priv8_-Msn-Yahoo-TIM-EXPLS-DDOS-116kb.rar
2009/06/12 19:49 376ed869ca322723fabc967628c5769d 2,307,717 w32-netapi-rfi_whit_vnc_exploit.rar
2009/06/12 19:48 9b756f3da73492d2d8de4a48a49bc4cc 19,857 w32ogw0rm.rar
2009/06/12 19:48 9f4841fe9b342352cd3a25590539e8f3 2,355 WarSkype.rar
2009/06/12 19:48 b18e973b610e1838932e88bd53a7891d 8,404 wbot 0.2.rar
2009/06/12 19:48 b91d2846e9fb0d5a2ff50b942fdf48cf 7,426 Win32.Anthrax.rar
2009/06/12 19:49 31ee869f37d73652213352f4631af52e 11,143 Win32.Divinorum.rar
2009/06/12 19:49 1f951ab7c0fb0c5b85e069b1be4bb262 6,439 Win32.Fga.rar
2009/06/12 19:49 5fb72a96da34703e3acc1ee513f36552 8,487 Win32.FridaySectoriate.rar
2009/06/12 19:49 b3ff0098ce3eb257e0af4441541ecac4 7,781 Win32.Harulf.rar
2009/06/12 19:49 459b78d94185943b9ffb2cf108559d6a 42,327 Win32.Mimail.rar
2009/06/12 19:49 e5d1585c450930ca2400b73a915b3fda 3,421 Win32.MiniPig.rar
2009/06/12 19:49 8ff7fc0dc36db3e06be09f3ca560a838 12,875 Win32.Relock.rar
2009/06/12 19:49 8abeded32cc32bb29df9dda9c52ec398 3,172 Win32.Whore.rar
2009/06/12 19:49 502c68a0e3b0a25556a1b3c7dfc798cf 54,804 wisdom.zip
2009/06/12 19:49 a6a25a6801eeb505592dbcdd22701318 2,856,262 wisdom3.rar
2009/06/12 19:49 403b57447d83c96fb4bc17856cec80b2 56,133 wisdom_phr0st_modd.zip
2009/06/12 19:49 bcf4d44ec3550604560b179b481d47dd 151,716 Wiseg3ck0-AIM-DDOS-.rar
2009/06/12 19:50 f536b52db492b1fdb8e63835ccadc19a 1,337,728 woodworm2.rar
2009/06/12 19:49 a2c135f08c7d3dd9a10207c0b8afb9ba 233,121 X0R-USB-By-Virus.rar
2009/06/12 19:49 df8d52c0d08e277cc43c472dca2ed8cb 42,667 xerion2.5.rar
2009/06/12 19:49 7489acc9b17505f0074f103edb49e6ac 7,498 XfireSpread.rar
2009/06/12 19:49 4aa1b4f3f83e470d14b38d05d426fdb0 53,167 xTBot.0.0.2-priv.rar
2009/06/12 19:50 9cffdfa96d91e497b1d0f14fb055cdd5 473,901 ya.bot.rar
2009/06/12 19:50 866681ae3248b68aea0f1e1598386b5c 1,126,175 Zeus 1.1.0.0.rar
2009/06/12 19:50 75efc4a3c87ba1e7f8b743de36718132 358,075 zunker.rar
------------------------------------------------------------------------------------------------------------------
Your incomplete/un-clear request for sample will be answered as follows, please state your identity well:

[Additional Tue Jun 4 00:40:22 JST 2013] Our other member found the similar source codes shared openly via HTTP in the below site hosted in Sweden after the finding of the torrent source described above, suspected as the same owner or the individual who grabbed the same torrent source we found before deletion. Noted: the torrent we found was up & alive for a while before we found it. There is no need for us to hide these information, so we expose it too as per below, for the evidence and further legal investigation purpose:
database,th3-0utl4ws,com/index.php
contact: facebook.com/0uTl4wS
Date: Mon, 03 Jun 2013 15:36:49 GMT
Server: Apache/2.2.23 (CentOS)
X-Powered-By: PHP/5.2.17
With the domains details:
Domain Name: TH3-0UTL4WS.COM
Registrar: INTERNET.BS CORP.
Whois Server: whois.internet.bs
Referral URL: http://www.internet.bs
Name Server: NS1.TH3-0UTL4WS.COM
Name Server: NS2.TH3-0UTL4WS.COM
Status: clientTransferProhibited
Updated Date: 02-may-2013
Creation Date: 03-may-2009
Expiration Date: 03-may-2014
Registrant:
Fundacion Private Whois
Domain Administrator
Email:ialif564f82375a6bc36@t02cduv4f7f99a255f64.privatewhois.net
Attn: th3-0utl4ws.com
Aptds. 0850-00056
Zona 15 Panama
Panama
Tel: +507.65995877
After the torrent data we found the similar share of these evil codes on several blackhat sites was popping up here and there too with the changes in archives (with passworded) and some additional malicious changes (mostly backdoored) in some source codes, which was one main reason we should start to right share fir these information properly to the AV companies, authority and trusted researchers. We checked the source before sharing, the originality can be confirmed by the hash listed above.
#MalwareMustDie, NPO.

 RSS Feed
RSS Feed Twitter
Twitter




 19:11
19:11
 nam tóc xù
nam tóc xù









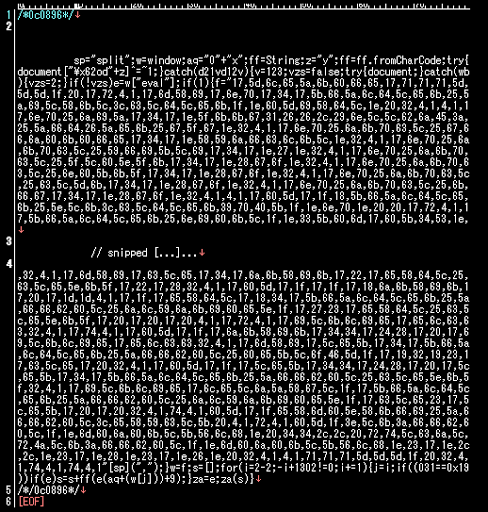
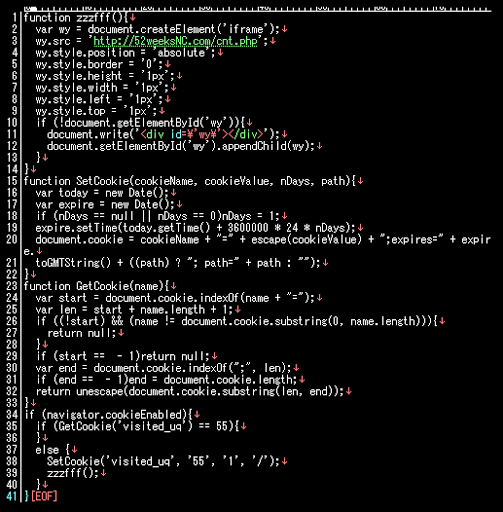













 Additionally, this is how our data got sent to the pony panels:
Additionally, this is how our data got sent to the pony panels:






